The October 2016 (DynDNS) DDoS Attack
A few weeks ago, a DDoS attack crippled the internet, affecting websites like Amazon, eBay, Twitter, and many, many more. It seems this was accomplished by turning IoT devices into a botnet. Most internet users know that these words exist, and they know that they mean things, but few actually understand what happened. So that’s what I’m going to talk about today. I’m going to break down the attack and offer suggestions on what can be done about it.
Let’s start with an introduction to the internet. Every website you visit is stored on a server somewhere. The HTML file, the images, the CSS, the JavaScript. All of it. So when you are visiting a website, you are loading files on a server.
Each device on the internet has an IP (internet protocol) address. Think of this as the device or server’s phone number. Each website has it’s own IP address. Each phone has it’s own IP address. If you are using your phone, and change from one network to another, you’ll get a new IP address. It’s the internet’s way of detecting who is who.
But if every time you wanted to buy something from Amazon, you had to go to http://152.134.189.104, and if you wanted to check your bank account, you had to go to http://147.543.146.324, etc. You’d quickly forget which IP belonged to which website. And those are IPv4 addresses. Those are all taken, so we are slowly switching to IPv6, with addresses that look like this: 2031:da8:a1b:14f0::1
Enter domain names. Domain names are easy to remember. Things like “amazon.com” or “ebay.com” or “chrisasbury.com”. Sadly, the servers that run the websites still operate using IP. Thus, we need a method of translating “domain name” to “IP address”. This is what a Domain Name System (DNS) Nameserver does. Think of it as a huge Rolodex that points each domain to the correct IP.
Site note: There’s a lot of fun things you can do with this. There are levels of DNS servers. For instance, I use an Active Directory Domain Controller at home. All of my computers use my ADDC as their DNS Server. It, in turn, uses my Ad Blocker as a DNS, which, in it’s own turn, uses my router for DNS requests. That means, I can intercept and redirect traffic. Take, for example, the Ad Blocker. I hate ads. Hate hate hate hate HATE ads. So when a website tries to load an ad, the transaction looks like this. “ad.domain.com” > DNS > “IP address of ad”. But my Ad Blocker recognizes that it’s an ad, so instead of loading the IP address of the ad, it loads a blank image.
Every time you visit a webpage, it takes up a little bit of bandwidth. It’s a microscopic amount, in the big picture. Most websites can handle millions of page hits per day. But there is a limit. Think of bandwidth as a freeway. It is meant to handle 1000s of cars, but if they all are trying to drive at the same time, the traffic will slow down. This is the basis of the DDoS (Directed Denial of Service).
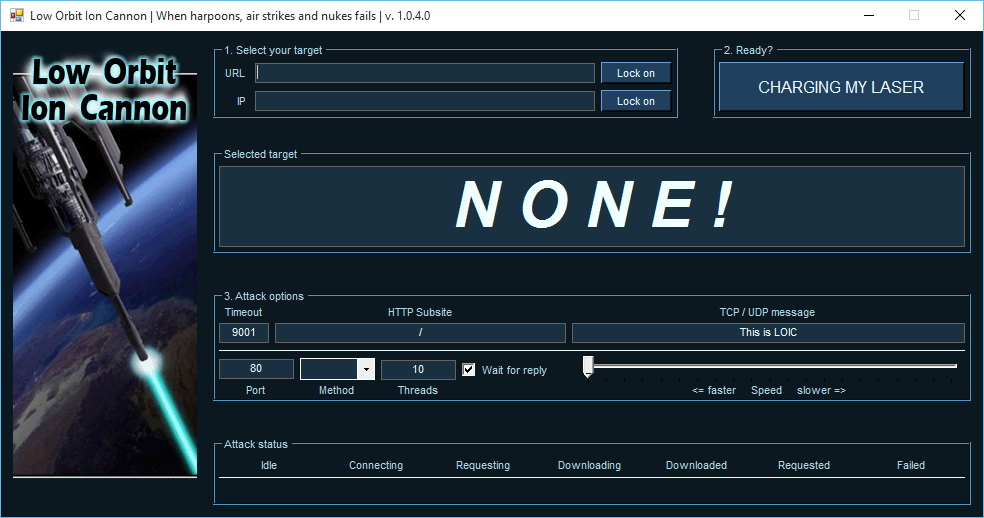
Back in the long long ago, maybe the early 2000s, hackers used the LOIC (Low Orbit Ion Cannon). It was a silly name, but the program worked pretty well. Anyone who had it running on their system basically turned their own system into a voluntary botnet. The system would then flood websites with fake page requests. Each page request was another car on the highway. If you got enough people to use the LOIC at the same time, you could take a website down. It would send hundreds of requests from hundreds of users, and websites just couldn’t deal with that much traffic. Actually, a better car analogy, would be if each request was another car… in the websites’s driveway.
To fight back, websites got better at recognizing “real” connection requests from DDoS attacks.
What if there was a more powerful attack you could do? What if, instead of targeting specific websites, you went after the DNS servers themselves? That’s what happened in the October 2016 attack. They went after DynDNS, which offered DNS services to a huge chunk of websites. So by DDoSing the DNS servers, they could also take down any other website that used that DNS server. They didn’t just flood the website’s drive ways with cars, they flooded the internet highway itself. So real traffic couldn’t get through to get to the driveway at all.
Surely, though, a DNS Server would be able to handle more traffic, right? Yup. So how did the hackers do it? Well, when you look around your job, or apartment, or whatever, you see lots of internet connected devices. Not just your computer or phone. Many security cameras are connected to the internet. I just made a Smart Mirror that is connected to the internet. With the Raspberry Pi, and Arduino, you can make everything from smart gardens to fancy clocks.
The hackers found out that many of these IoT (Internet of Things) devices used a particular part from a particular manufacturer. And they had a hard wired default login. Like, the user could go into the web interface and change the password for themselves, but there was an additional login at the hardware level, that only the manufacturer could access. At least, until the hackers found out the login information, and used that to turn these devices into a botnet.
A botnet, by the way, is when you have a huge number of computers (net) and they act as robots (bot) to do the same thing at the same time. Bot+net=botnet.
The hackers used the default logins to upload a malicious script into the RAM of these devices that instructed them all to begin a DDoS on command. So all of these smart devices started asking DynDNS to load pages at the same time, and DynDNS just couldn’t handle it, which meant that it couldn’t direct users to the correct IP addresses, which meant that when you tried to connect to Netflix, the page wouldn’t load, which meant that binge watching Stranger Things was not an option.
And the internet wept.
So what can we do about this? Well, for one, the attack loaded the script into RAM, so unplugging the devices from power for a few seconds should remove the script. But, the default login is the same, so the attackers could just load it again. What we really need to do, is force regulations on the makers. There are two reasons there would be a hardware login. One, it’s so the manufacturer can force updates. Two, it’s a backdoor. Neither of these is a thing that needs to happen. If it’s a backdoor, it’s bad times. If it’s to force updates, they can just switch to letting the users run the updates.
I’ve heard some suggestions of having a network wide antivirus that would scan all of the devices on your WiFi router or whatever. I think that’s a great idea, and hope it happens.
The main problem is that attackers use the system against itself. It’s like saying that the best way to stop a heart attack is to not have a heart. You kind of need it. Well, we kind of need DNS, so we can’t get rid of it. For now, we can make sure that the devices we buy do not have default logins, come from reputable companies, using reputable parts. Turn the devices off when not in use. Maybe ISPs can get better at detecting DDoS attacks. And hope for the best.



One Comment
Pingback: