Password Hygiene
I’ve been meaning to write this for a while, but I never have time. Think of this as a tutorial, rather than a rant. Today, we’re going to talk about password hygiene. Password hygiene is the process you use to keep your passwords safe. It’s just as important as brushing your teeth. Your passwords control all of your online life. You login to just about everything. Your various accounts have all kinds of information on them. Imagine how much about you someone could learn, if they read through your email. Or your Facebook account. Or your bank account. I’m not even talking about the damage that could be done. I’m just talking about the things about your life people could learn. Do you really spend that much on coffee? Do you follow that many meme pages?
So today, let’s talk about my method for password security. First, let’s understand what we’re up against. In this context, there are three main attack vectors. A dictionary attack is when the attacker has a list of common passwords, and tries each one until they get in. Wikipedia even has a list of the 10000 most common passwords. But security researchers update lists like these frequently. Next, we have the brute force attack. This is where the attacker tries every possible combination until they get in. AAAAA, AAAAB, AAAAC, etc. Lastly, we have the social engineering attack. This is where the attacker gets to know as much about you as possible, in hopes that they can guess your password.
Now that we know how an attacker can get into an account, let’s look at the defenses against them. The dictionary attack has one simple weakness. The password needs to be in the dictionary. Not an actual dictionary. The list of passwords is called the dictionary. So as long as your password isn’t common, and hasn’t been leaked on the internet somewhere, this attack probably won’t work against you.
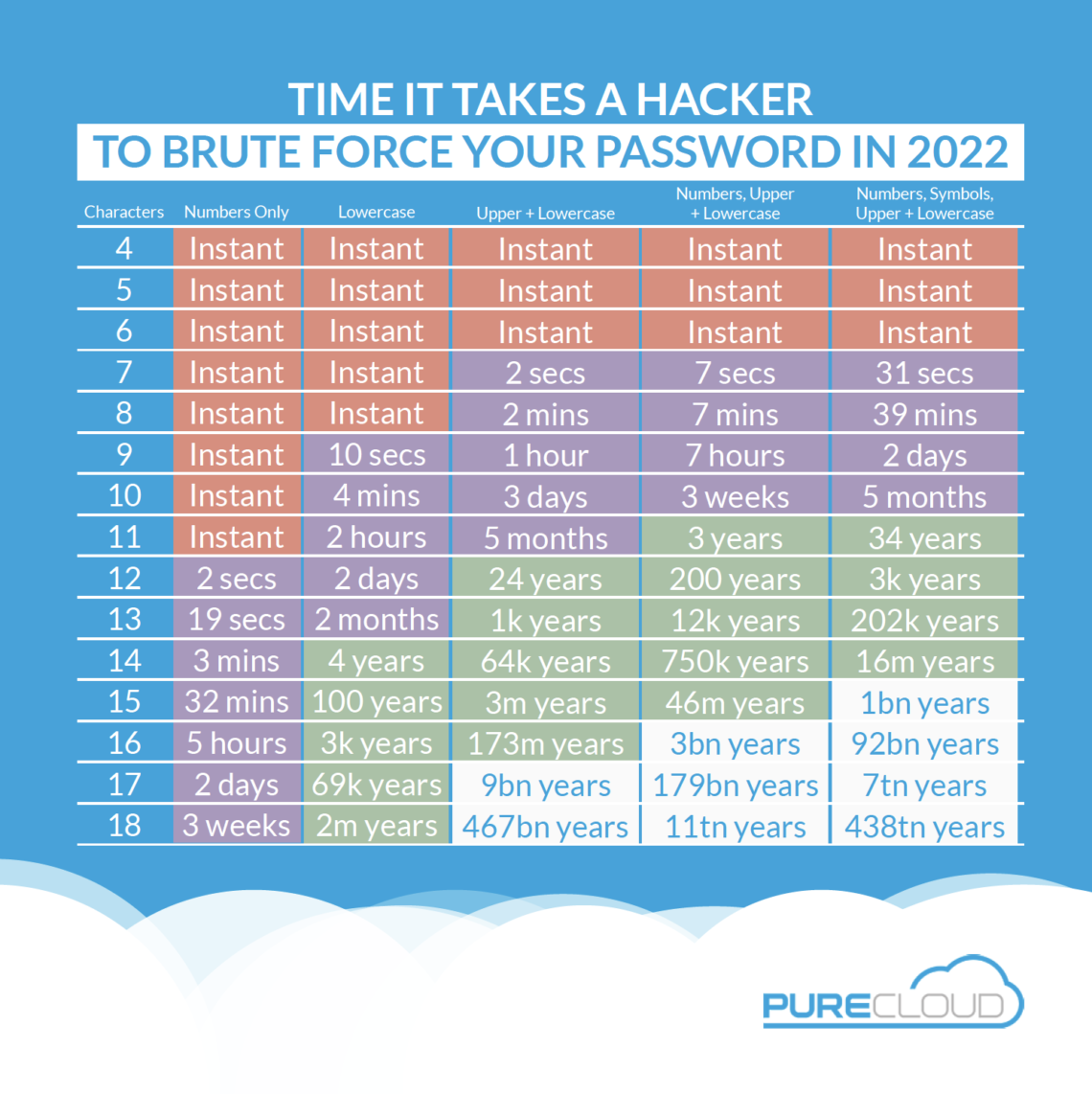
The brute force attack’s weakness is time. It takes time to try every combination. The longer the password, the longer it takes. For instance, a password that is 10 letters and numbers (no special characters) would take 4.4 seconds. Simply adding a special character bumps that up to 44 seconds. 16 characters (with special characters) takes 47 hours. Adding one more character, pushes it to 5 months. So longer passwords increase the time it takes to crack exponentially. You can visit this website to check your password. But don’t enter your actual password. Change a letter or number with a like letter or number. If your password is ChrisIsCool4, change it to KhrisIsKool5.
Social Engineering is more difficult to defend against. We are social creatures. We like sharing our interests and hobbies with others. The best advice I can give here, is to not use passwords close to you. Don’t use important dates. Don’t use family or pet names.
There’s one more important thing to keep in mind. Password reuse. I know. It’s difficult to remember a bunch of passwords. But here’s what happens. You use the same password on everything. One random account that you forgot about has a breach and that password and your email address gets leaked. Then an attacker uses that password to get into your email. Then they use a password reset function on Facebook, which sends the reset to… your email. That they’ve already compromised. This happens all the time. DO NOT REUSE PASSWORDS.
With all that said, we need long passwords, that are not common, can’t be directly linked back to us, and are different on each service.
How? Here’s my process. First, I use a password manager. There are a bunch of them. Most have a free and a paid version. Each has it’s own set of features. For what we need, pretty much any will do. I use KeePass because it’s open source and is cross platform (so you can use it on your phone, your Windows PC, your Linux laptop, and that Mac that’s collecting dust in the basement because that’s all it’s good for). Password managers work in basically the same way. They create a vault. You save each login in the vault. The vault is encrypted. The only way to unlock the vault is with a master password. Once unlocked, you can copy and paste the password from the vault into the website. This does a few things. First, you don’t have to remember passwords anymore. You only need to remember the master password. So go crazy. Make a 25 character randomly generated password. I don’t know any of my passwords anymore. They are all random. Now we’ve eliminated the dictionary attack as a threat, a brute force attack would take 99 MILLION years, and social engineering won’t work because how often do we talk about the latest sports match featuring star player “asdfasdfas1@rt5y5fk63#r5”?
But what about our master password? We still need a long, not common password, that can’t be guessed. That’s where l33tspeak comes in. L33t speak is an old internet slang, common on nerdy message boards back in the long long ago. It’s where you replace letters with numbers (and sometimes special characters). For instance, “password” could become “p4ssw0rd”. Here’s how you could do it. Take your favorite movie, or book, or whatever. Find a lesser known character in it. Let’s say Grimaud who was Athos’ servant in the Three Musketeers. Even if you talk about how much you love the Three Musketeers, no one is going to assume that Grimaud is your favorite character. Now, let’s convert it into l33t speak. Gr1m4ud. We need a special character or two. How about Gr1^^4ud.
Grimaud would take 15 minutes to crack. Gr1m4ud would take 1 hour. Gr1^^4ud would take 47 years.
Ok. We have a very secure password that we can remember. It is not common, would take a long time to crack, and isn’t easily guessed. The rest of our passwords are stupid long and each one is different. We are doing great. But we can go further.
2fA (dual factor authentication), or MfA (multifactor authentication) is where you login successfully, but then to prove you are you, you also have to give a rotating single use code that is generated in a different way. Maybe it’s a code sent as a text. Maybe it’s emailed to you. Maybe you use an app. Maybe you use a special USB devices. Whatever the case, if the attacker doesn’t have access to the code, even if they do have your password, they still can’t get in.
Like password managers, authenticator options are quite numerous. Most companies are discontinuing email codes, and I’d suggest using text codes only as a last resort. I use Authy*, but there are a bunch of apps out there. I also like YubiKey, which looks like a USB drive, except it’s only purpose is to generate codes. Let’s stick with Authy for now. Note, that password managers are starting to offer 2fA as a bonus feature. I’d actually suggest not doing that. Having two separate apps means that if one has an issue, that doesn’t mean you’re locked out. Setting up 2fA varies depending on the service, but the basic idea is that you scan a QR code, which generates a code. You enter that into the service. Then you’re done. Each time you login, you’ll open the authenticator app, enter the code, and that’s it.
Update 6/17/2025: Authy dropped support for their desktop option. That sucked, but it’s fine. Then they dropped support for GrapheneOS. That was a dealbreaker for me. I have switched to Ente Auth. So far, I’m quite happy with it. It’s free, open source, and has a desktop option as well.
I know it seems like a monumental task. I know it seems like a hassle, especially when you have 2fA. But if you follow my advice above, the chances of one of your accounts being compromised drops to virtually nothing. With one extra caveat. Change your passwords at least once a year. This is easy for most passwords, because they are randomly generated as it is. Changing it to a different random string of letters, numbers, and symbols is easy. However, you should also change your master password frequently as well.
Lastly, I suggest signing up for alerts from Have I Been Pwned. This is a free service that scours the internet (including the dreaded dArK WeB) for your email address. If it finds it, you’ll get an alert that tells you what was compromised, and what information was leaked. That way you can change the password for that service if needed.
Stay safe out there.


