Technology
-
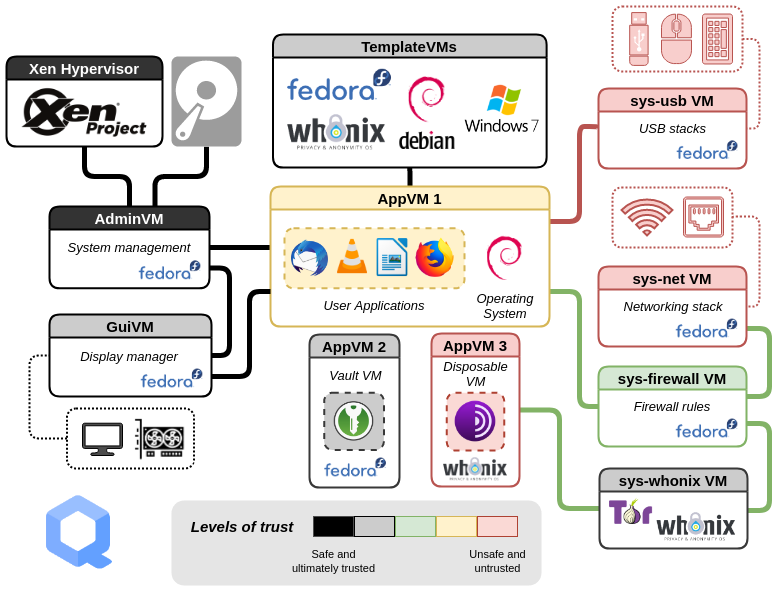
QubesOS
In my Server series, I mentioned that I use QubesOS as my daily driver. So I decided to write about my experiences using it for the last two years. Keep in mind that I’m not a cyber security professional. I’m just a nerd with a lot of free time. I love Qubes, but there are certainly some issues, and a steep learning curve. If you’ve used Linux regularly, you’ll probably adapt pretty easily. If you’re coming from Windows or the one that the children use (Apple), you’re going to end up frustrated and give up on it. Which is disappointing, because it’s a really intriguing concept.
-
The Craziest DIY Chandelier
Today, I’m going to show you how my girlfriend and I made the craziest chandelier using rope lights, some stiff wire, and elbow grease.
-
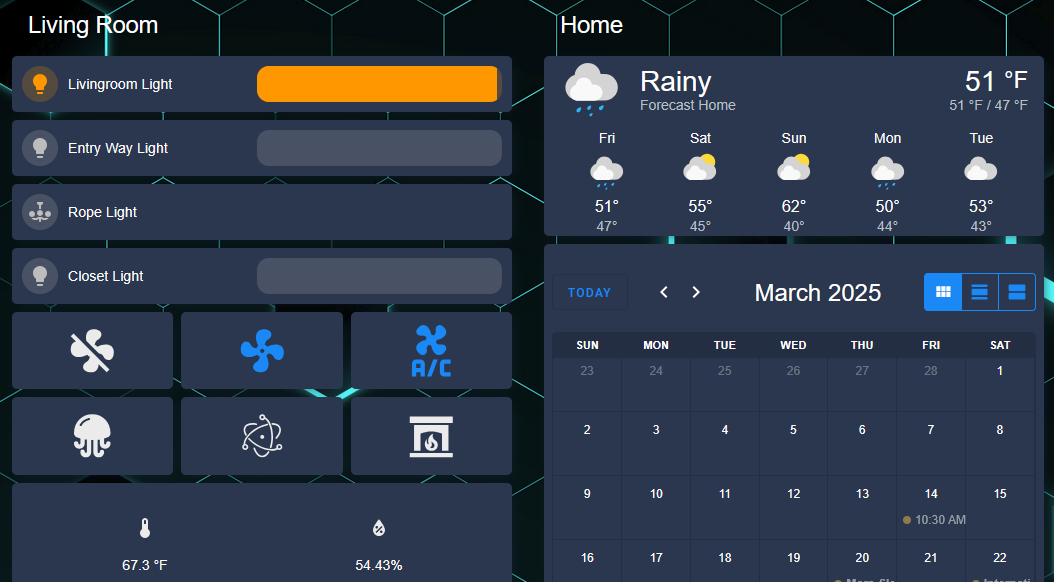
Server Build 2.0 Part 4 – HomeAssistant and Security Cameras
Now that we’ve setup our new server, created firewall rules, and created our VMs and Docker containers, it’s time for something new. HomeAssistant is a home automation platform. It’s highly modular and very actively developed. It’s opensource, and there are nerds all over the world contributing. Instead of being limited to devices that are “approved” to work with Alexa or Google Home or whatever Apple’s dumb version is called, you can get almost anything to work with HomeAssistant.
-
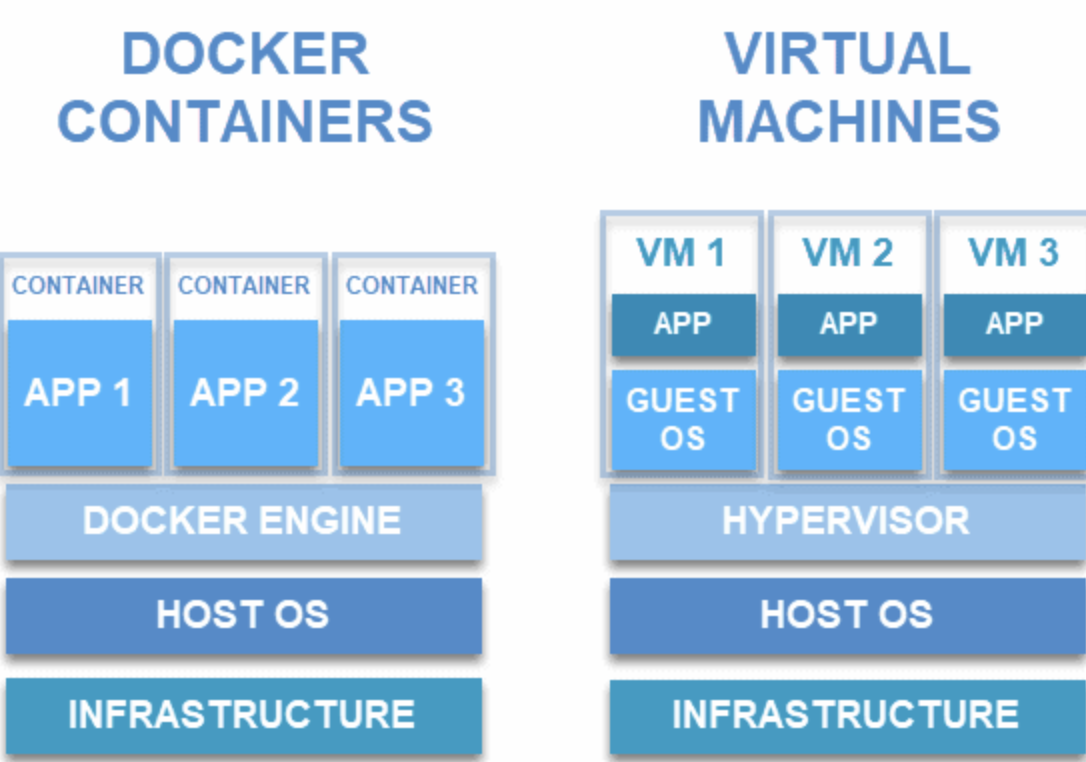
Server Build 2.0 Part 3 – Proxmox and Docker
Previously, I talked about setting up the network in my new homelab. In this article I’ll briefly cover Proxmox, and how I have it setup, but mostly talk about Docker and some of the fun and neat things I do with it.
-
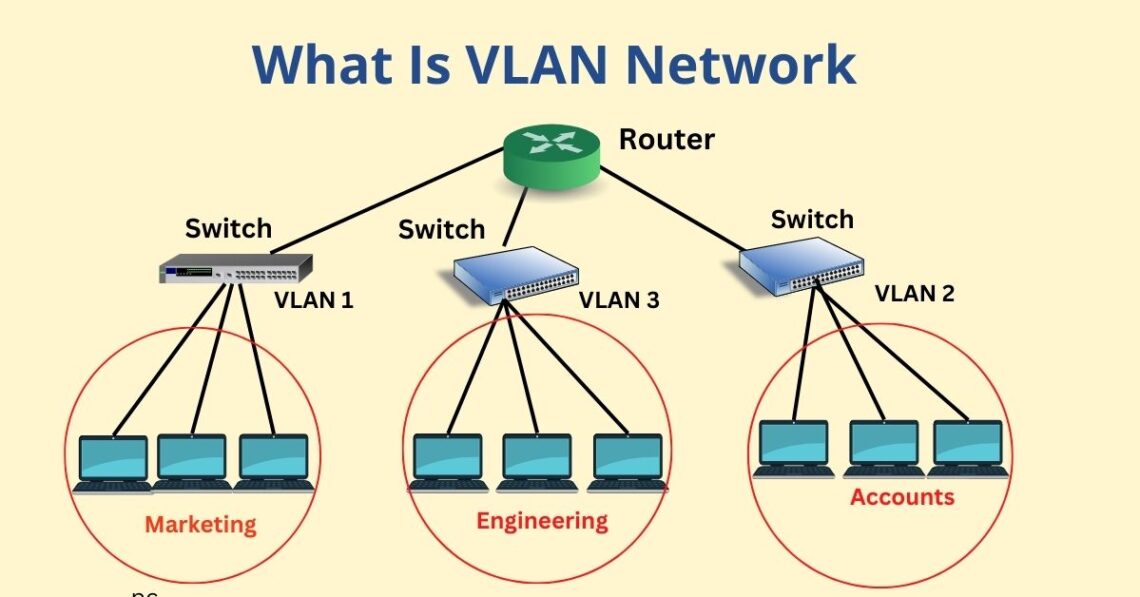
Server Build 2.0 Part 2 – pfSense and HAProxy
In the first segment of this new series, I gave you a quick rundown of the changes since my first home server 10 years ago. Now let’s get into the fun stuff. VLANs, reverse proxies, and firewall rules, oh my. Originally I had a Netgate SG1100 firewall. It worked fine, but eventually the hard drive failed. It was also underpowered for my new gigabit speeds. I could buy a new one, but what’s the point. I didn’t want to spend the crazy money for an enterprise level firewall. So I got a Beelink mini PC.
-
Server Build 2.0 Part 1 – Updates
Roughly 10 years ago, I wrote a series of articles walking you through the process of setting up a home server. Over time, my needs changed, as did the available technology, as well as my knowledge. So in the next few articles, I’ll be writing a follow up, but it’s really starting from scratch. This specific article is more of a catch up, that fills the gaps between then and now. This will seem like it all happened at once, but this really spans years. The old articles are still accurate. Installing a system is installing a system. I just learned how to do more and new things. All of…
-
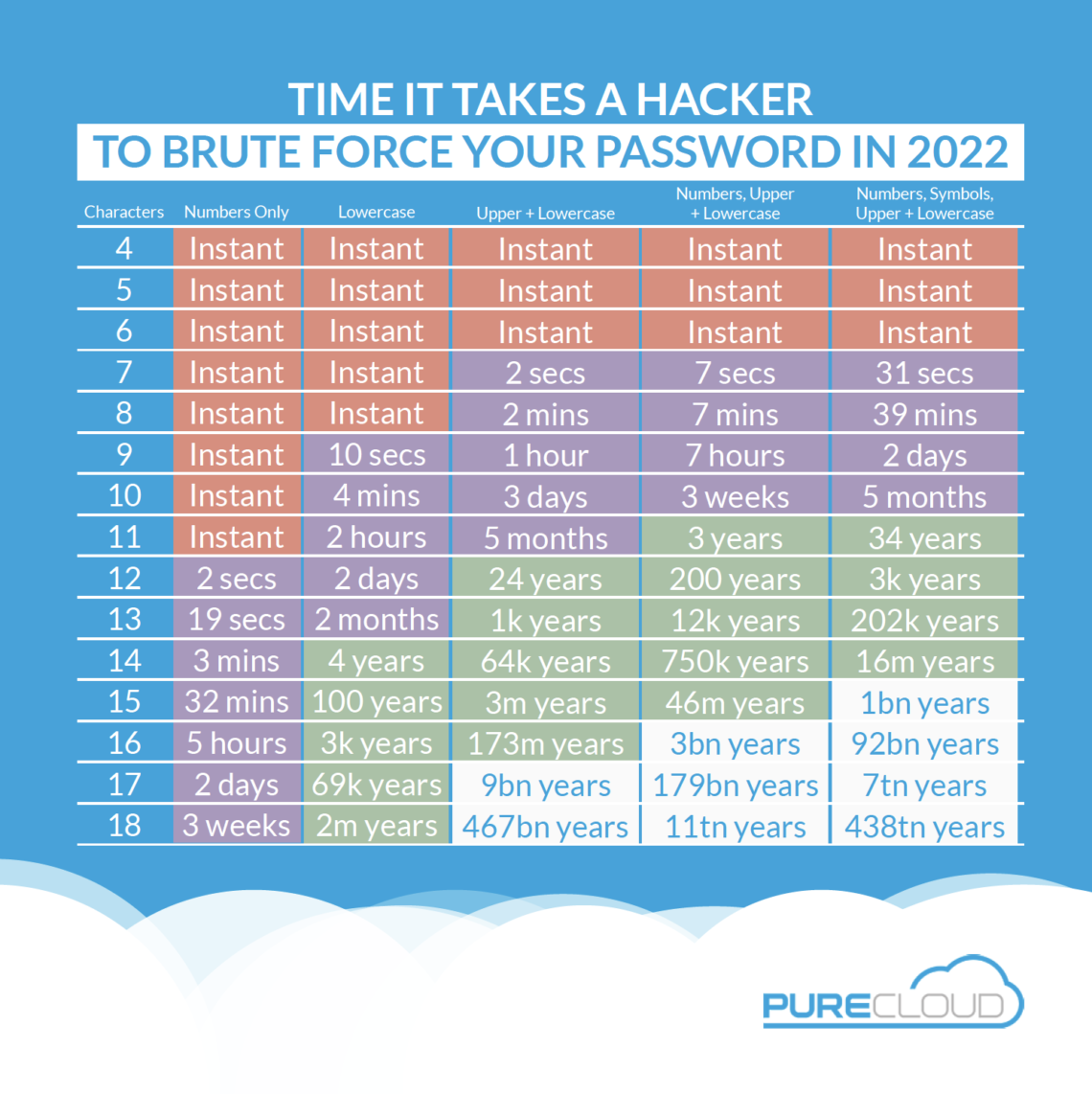
Password Hygiene
I’ve been meaning to write this for a while, but I never have time. Think of this as a tutorial, rather than a rant. Today, we’re going to talk about password hygiene. Password hygiene is the process you use to keep your passwords safe. It’s just as important as brushing your teeth. Your passwords control all of your online life. You login to just about everything. Your various accounts have all kinds of information on them. Imagine how much about you someone could learn, if they read through your email. Or your Facebook account. Or your bank account. I’m not even talking about the damage that could be done. I’m…
-
Protect Your Privacy with a Secondary Email Address
Many moons ago, I signed up for a website called Have I Been Pwned. This website tracks your information, and if it shows up in a leak or hack, it notifies you. It’s a great tool, and I recommend you all use it, especially in our current times full of security breaches. Today, I got a notification that I had been leaked along with 1.4 billion people. Billion with a B. This leak included Full Names, addresses, IP addresses, etc.
-
Genetically Modified Organisms
GMOs. We’ve all heard the phrase. It’s some sort of nasty thing “they” are putting into our foods. They should put it on labels so we know what we are consuming. It’s unhealthy. It’s poison. It’s a plot by corporations to keep us docile. Or maybe it’s just food.
-
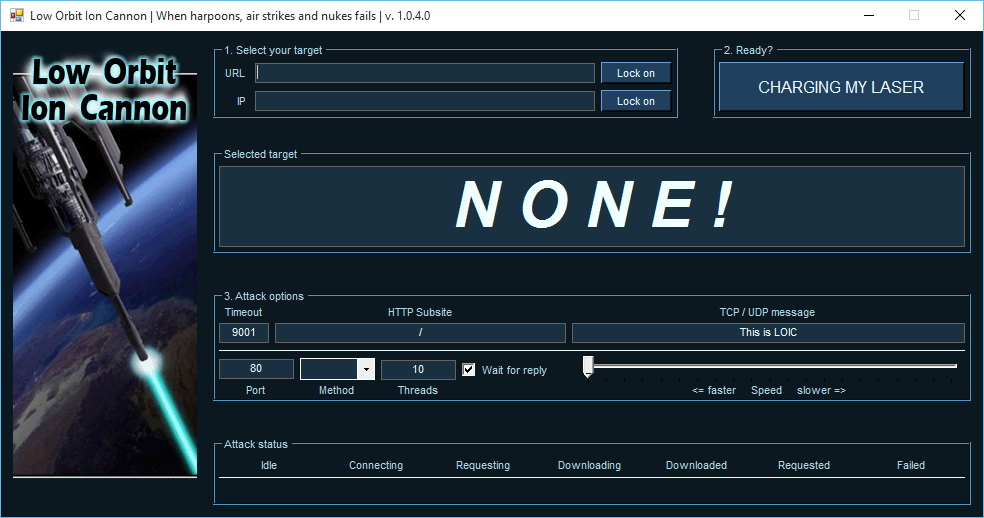
The October 2016 (DynDNS) DDoS Attack
A few weeks ago, a DDoS attack crippled the internet, affecting websites like Amazon, eBay, Twitter, and many, many more. It seems this was accomplished by turning IoT devices into a botnet. Most internet users know that these words exist, and they know that they mean things, but few actually understand what happened. So that’s what I’m going to talk about today. I’m going to break down the attack and offer suggestions on what can be done about it.