QubesOS
In my Server series, I mentioned that I use QubesOS as my daily driver. So I decided to write about my experiences using it for the last two years. Keep in mind that I’m not a cyber security professional. I’m just a nerd with a lot of free time. I love Qubes, but there are certainly some issues, and a steep learning curve. If you’ve used Linux regularly, you’ll probably adapt pretty easily. If you’re coming from Windows or the one that the children use (Apple), you’re going to end up frustrated and give up on it. Which is disappointing, because it’s a really intriguing concept.
Let’s start off with the basics. What is Qubes? It’s basically a hypervisor based on Xen. That means that it’s primary job is to run virtual machines. Oh. Side note, if you want a drinking game, take a shot every time I say “VM”, “Virtual Machine”, or “Qube”. Please don’t do this. You might die.
Anyway. In my interview with Shannon Morse, she mentioned that we each have to choose between convenience and security. Qubes very much errors on the side of security. It will chose security every time. It offers compartmentalization and different levels of persistence, so if one VM gets compromised, the rest of your system is probably safe. That doesn’t mean you should use that as your primary antivirus system, but it does help.
Here’s a reality you may not like. When it comes to your privacy and security, YOU are the weakest link. You could give me an unpatched Windows XP machine, and I’ll be fine. I don’t download untrusted files. I don’t go to fringe websites. I’m good. Conversely, I could give my super secure awesome laptop to the stereotypical grandma who doesn’t know how computers work, and it’s only a matter of time before it’s borked. Qubes does a lot of the heavy lifting, and gives you the tools you need to be safe, but you do have to meet it half way. Their tagline is “A Reasonably Secure System”. That’s basically lawyer speak for “don’t sue us if something goes wrong”, but it’s also the most secure system out there right now (that’s connected to the internet).
Real quickly, we should talk about hardware requirements. This is one of two major drawbacks to the system. It needs a ton of system resources. I have a 12th gen I7 with 64gigs of RAM . I’d say 32gigs is the bare minimum. They say you can run it on 16, but I can’t imagine that being an enjoyable experience. I also have two 4tb NVMEs in a ZFS or BTRFS (I can’t remember) RAID. That’s not required, but I figured I was starting from scratch, so why not. That basically means that the two drives are clones of each other. If one hard drive fails, I have a complete copy on the other drive.
The second major drawback is that in order to be effective, you have to rethink how you use the computer. Let’s consider a traditional computer. There are three basic layers. The hardware layer is anything that exists in our physical reality. If you can touch it, that’s hardware, even if you have to take the computer apart to touch it. Next you have the operating system (OS). That’s your main way of interacting with the computer. That would be your Ubuntu, or your Windows, or whatever Apple is calling their dumb system this year. Lastly, you have the software layer. That is the programs you use. Office, Firefox, solitaire, etc. When you move the mouse (hardware), Windows (OS) recognizes the movement and gives you a visual representation by moving the cursor. When you click, the OS sends the signal to the program (software) behind the cursor.
But you don’t think about any of that. You want the computer to do the thing, so you make it do the thing. It’s seamless.
The problem is that because those three layers are so intertwined, when one gets compromised, the entire system is potentially compromised. It happens all the time. You download a file in Firefox (software). The file is installed on the OS. The file contains a virus that activates your webcam (hardware). All three layers have been compromised. If only there were a better way.
That’s where Qubes comes in. Qubes allows you to isolate different things. Let’s say you have a “Personal” Qube, and a “Work” Qube. They don’t share a file system. If you get a virus on Personal, it doesn’t spread to Work. You can go even deeper. You can set a specific Qube to use a VPN. Or TOR. Or have no internet access at all.
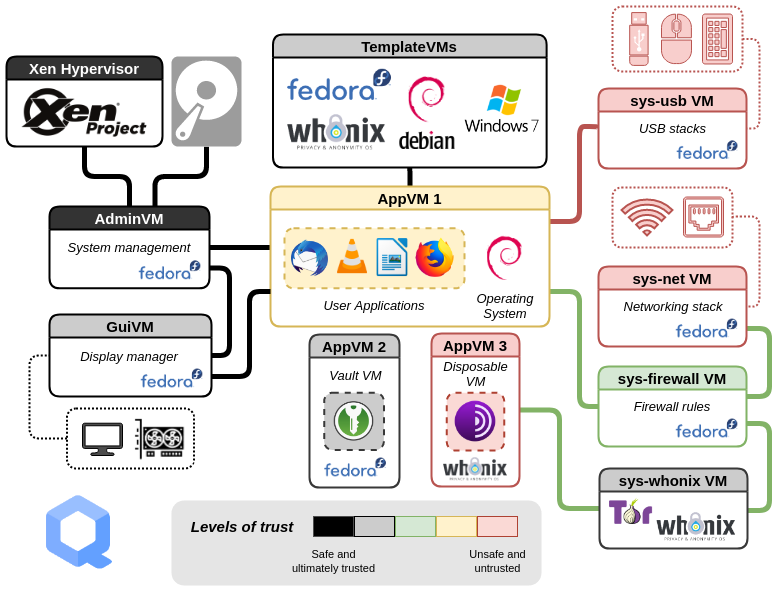
Let’s take a step back and examine Qubes structurally. (consult the picture at the top of this article) The… “heart” of the system is Dom0 (domain 0). This serves the same purpose as a traditional OS. It manages the display, and the cursor and stuff. Just like a traditional OS, if Dom0 gets compromised, it’s game over. Your system is now potentially compromised. Therefore, we want to protect it at all costs. We do this by disconnecting it from the internet. Even if you want to run updates, it actually downloads the update in a separate Qube, then copies it over. It’s also recommended that you never install any software in Dom0. You want to keep it as pristine as possible.
Next you have system Qubes. By default, you have sys-net, sys-firewall, sys-usb, and sys-whonix. The internet connects to sys-net. If an attacker gets that far, they’ll just see it as a Fedora system with very little on it. They won’t know that it’s just a VM attached to a bigger system. Then the internet is filtered through sys-firewall, which is, you know, a firewall. I added two extra system Qubes. The first is sys-adblocker, which is just Debian with pihole installed. Most of my other Qubes connect to that. I also have sys-vpn, which I don’t use often, but it’s there if I ever need it. I don’t use whonix, so I’ll skip it. But basically, that just routes the internet through TOR. USB devices are managed by sys-usb. If you had a virus on a USB device, and you plugged it into the computer, it can only get as far as sys-usb, unless you “attach” it to another Qube. You have to specifically allow a USB device to connect to whichever Qube you want. On my laptop, that includes the microphone and webcam.
This brings us to the concept of “persistence”. In this context, persistence is whether or not something survives a reboot. In Qubes, there are three levels of persistence. Full persistence means that everything is saved, and will still be there when you reboot that Qube. This is usually dedicated to full OSes, and acts like a standard virtual machine. Next, you have disposable Qubes. Files on these Qubes are completely erased upon a reboot. Things like sys-net, and sys-usb are disposable. Even if they get infected, all I have to do is reboot them, and the virus is gone. Theoretically. I haven’t tested it. Everything else is semipersistent.
 Let’s look at a standard file structure. I’m using a Windows layout so most people can follow along, but Qubes is based on either Fedora or Debian. The same logic applies. System files (like programs and the important stuff) are not persistent. That means that when you reboot the Qube, any changes are lost, and the prime version is restored.
Let’s look at a standard file structure. I’m using a Windows layout so most people can follow along, but Qubes is based on either Fedora or Debian. The same logic applies. System files (like programs and the important stuff) are not persistent. That means that when you reboot the Qube, any changes are lost, and the prime version is restored.
The user files, however, are kept. So you don’t lose your documents or photos or whatever. This means that even if you download a virus, if it infects the system files, the virus is wiped each reboot. Though, it could reinfect it from the user files, so you’d have to delete the download.
Almost all of the Qubes you use on a daily basis will be based on this concept.
In my case, I have a Personal Qube for day to day use. I have a Work Qube that I hardly ever use. I have an Art Qube for… art. I have an Untrusted Qube for anything I don’t trust, and I have a Vault with my password manager and important things. The Vault Qube has no internet access. Personal and Work go through the adblocker. Untrusted goes through the VPN.
But wait, I have all these Qubes I use on a regular basis. Does that mean I have to install and update each app multiple times? I’m too lazy for that. Here’s the magic of Qubes, and my favorite feature. Templates. Basically you create a template, and install everything in there. I use Flatpak, but you can also install software however you like for that system. I like Debian, so I could also use apt or dpkg -i. Whatever the case, you just install the software once. Then each of my other Qubes are based on that template. Another way to look at it is in the above image, “not persistent” is the template, and “persistent” is the Qube you actually use. When it’s time to run updates. Just update the template, reboot the other Qubes, and they’ll now be running the latest and greatest version of the software. I love it. Absolutely love it.
What about usability? When you first look at the desktop, you’ll see a standard desktop. You have a bar across the top with a menu of the programs and settings. It’s a little different because they are sorted by Qube, so Firefox (Personal) is different from Firefox (Untrusted). They are also color coded. At the beginning of the QubesOS project, Qubes used this color coding system to trigger something in the user’s brain. “Oh. This program is red. I should not enter important information in it.” “Oooo. This one is green. That means it’s probably safe.” It’s a good idea, but again, the user is the weakest link. It’s up to you to pay attention to the details. And this is where my previous comment about having to rethink how you use a computer comes in to play.
Let’s say you want to check Instagram. Well, Instagram has a lot of tracking cookies. So you’d probably want to run it in the Untrusted Qube. When you’re done looking at people’s food, you decide to check your bank balance. That should be opened in the Personal Qube. Oh. I checked my email, and there’s this attachment. I don’t trust that, so I better open it in a disposable Qube. Cool. It was safe. Now I can open it again in the Personal Qube. But actually, it’s work related, so I need to move it to the Work Qube.
This brings up a problem. Well, not a problem, but an extra step. If you have two Qubes that are isolated, how do you copy and paste between them? Copying text is easy. You just add a step. Instead of just CTRL+C, you have to do CTRL+C to copy the text. Then CTRL+SHIFT+C to copy it to the global clipboard. Then you click on the Qube in which you want to paste the text. CTRL+SHIFT+V to paste from the global clipboard. Then CTRL+V like normal. Once you get the hang of it, it adds almost no time. It’s a really easy habit to form. To transfer files, you have to right click on the file, and select “Copy/Move to Qube” and select the Qube. Then on the recipient Qube, you’ll have a folder called “QubesIncoming” and the file will be in there, sorted by “donor” Qube name.
The system is highly highly super duper highly customizable. You can make and delete as many templates and Qubes as you want. If you’re a lawyer, you could create a separate Qube for each case. If you’re an artist, you could create a separate Qube for each client. If one client requires you to use one VPN, and another client wants you to use a different VPN, you can do that. Once you do the initial configuration, it’s pretty much set and forget.
What about programs? You can create templates from a bunch of different OSes, but the most common are Debian and Fedora. Almost all of them are Linux based. Which means you are limited to programs that run on Linux. Instead of Adobe InDesign, you’ll use Scribus. Instead of Microsoft Word, you’ll use Libre Office Writer. It is technically possible to run Windows as a standalone VM, but then you lose all the fun security and isolation options. Plus, and this is anecdotal, but my Windows VM crashed on me (it was the program I was using’s fault), which in turn crashed Qubes, which fucked it up so much, that I had to reinstall the entire system. It was… not fun. Apple is not possible to run on Qubes. But if you have the IQ to use Qubes, you probably don’t use Macs anyway.
So you install all the programs you want in the template. Then you can pick and choose which Qubes have shortcuts to each program. For instance, I want Firefox in all of my Qubes, but only want my Art Qube to have Inkscape. You can easily add or remove the programs from each Qube. This mostly just cuts down on the list in the menu.
Some have complained about computer speed, since each Qube is a separate VM. Sure, there’s a slight wait when you first start a Qube (I’m talking less than 5 seconds), but once that VM is running, opening any program in that Qube is the same as a traditional computer. This is where you’ll most notice how much RAM you have. The more RAM, the more things you can have running.
So is Qubes right for you? Honestly, probably not. Almost exclusively because of how confusing it seems at first. I actually named my Qubes computer Daedalus, because in Greek Mythology, he created the Labyrinth. Sometimes using Qubes feels like that. However, it’s a really solid concept, and I hope other systems implement some of it’s ideas. Or, perhaps, Qubes will become more user friendly. If you’re a spy, or a journalist, or a government official, or someone who has a high risk of being targeted by hackers, or if you have access to important information, you might consider using Qubes. It would be a great option for you, but you’ll have to put in the work. For me, I like tinkering with things, and I’m very familiar with virtual machines. After 2 years, of using QubesOS as my daily driver, I’m still happy with it.
Oh. Also, if you played the drinking game… you need to go to the emergency room stat. But if you were just curious, the final count of times I said “VM”, “Virtual Machine”, or “Qubes” in the article is… 77.


